Desktops, laptops, tablets and smartphones all offer capabilities that accountants could only dream about in past years. But those capabilities come at a price. Breaches, data theft, viruses and ransomware all come along with the benefits. Cybersecurity — keeping your data and that of your clients safe — has to be a concern, and one that has to be continuously addressed as more and more vulnerabilities are discovered and new threats continue to emerge.
Without proper precautions, it’s almost inevitable that you’ll get burned. And as attacks get ever more sophisticated, the precautions you have to take need to be more sophisticated, too.
Restricting physical access to your computers and other computing devices is just the first step. But with most if not all of your devices connected to networks and the internet, it’s not enough.
As to what kinds of risk, and how to handle the threats to you and your clients’ data, we went to several software vendors and well-known consultants to get their insight on the growing threat and what measures you can employ against them.
Where are you vulnerable?
As PCs and other devices have become more plentiful, and more people become more knowledgeable about how they work, a constant back-and-forth has developed between people developing new ways to disrupt other users’ use of PCs, and companies being created to deal with these attacks. Today, there are more ways than ever that your PC can be breached and that your and your clients’ data can be destroyed, exposed and compromised.
Threats abound everywhere. According to James Bourke, a partner and managing director of advisory services at Top 100 Firm Withum, “The biggest threats to CPAs are those involving unauthorized access to their client’s data. Those threats come in the form of phishing attacks, malware attacks, and other techniques used to gain unauthorized access to this valuable data.”
And Tom Kelly, senior director of product management at Oracle NetSuite, added, “Outdated software can be a significant issue that can increase the success rate for malware and ransomware — especially for small to midsized companies that don’t have a robust IT department.”
There are other common areas of vulnerability, according to Stephen Lawton, special projects director at cybersecurity information publisher SC Media: “The biggest cyberthreat facing accountants are the business email compromises where an attacker pretends to be a client and directs the accountants to take a specific action. It could be to redirect a payment to a new bank account number or perhaps telling the accountant that there is a new business partner or client who should be paid on a regular basis. Another serious threat to a company is often its lack of staff training in cybersecurity. User error should be expected, with an incident response plan in place. Training your users to question every email and to not click on links is essential.”
Phishing is aptly named, with invaders trolling for information they can use to breach client files and financial assets. Another frequent consequence of clicking on an email from someone or some organization that you’re not sure of or think is legitimate is introducing malware into your system and network. Often these emails look official, as if they come from a source you might have a relationship with. As an example, answering an email from “Apple” telling you that your account is frozen unless you update your information, can result in you or a staff member simply handing over access credentials and other sensitive information.
“Often, the easiest way attackers enter a professional organization is through what appears to be an expected email,” said Lawton. “It might not be a direct attack against an accountant but rather an emailed ‘resume’ to HR or what appears to be a benign email with no attachments but rather a link to an infected site.”
Thomson Reuters’ Trenda Hackett, a CPA and senior technical editor in the tax professionals segment, pointed to a recent study that indicated that mobile phone account takeovers are on the rise.
“According to the IRS, between five and seven tax firms are reporting a data breach each week,” said Hackett. “Phishing continues to be the No. 1 way that cybercriminals are stealing taxpayer information. The IRS reports that 91 percent of data breaches of tax professionals are the result of an employee opening the infected attachment of an email that appears to be legitimate. When the attachment is opened it infects the device with malware.”
Ransomware is another problem that our respondents pointed out. “Ransomware is a type of malware that infects computers, networks and servers, and encrypts and locks data,” Hackett explained. “Cybercriminals then demand a ransom to release the data. Users generally are unaware that malware has infected their systems until they receive the ransom request.”
Brian Diffin, chief technology officer at Wolters Kluwer Tax Accounting, added some additional points of vulnerability. “Some of the biggest cybersecurity threats observed today, that can result in criminal activity and impact accounting firms, include outdated or unpatched software — operating systems, software applications, browsers, firmware and middleware, anti-virus software, endpoint detection and response solutions that can leave firm’s systems open to attacks, and data breaches caused by employees, especially when personal device use for work-related activity is permitted. Former employees can also be a threat, if IT termination processes are not well defined and rigidly practiced.”
Other weak points can include single-factor authentication protocols and weak passwords that can be uncovered with automated tools that use a combination of dictionary words and numbers to crack them and weak perimeter defenses, he added: “Firms should be deploying advanced firewall approaches and solutions, not allowing any open access from the internet.”
The right tools
Looking at all the ways your systems can be attacked can be daunting, but having the right tools can even the odds. Access control is one major way to protect yourself. If they can’t get to your system, they can’t break into it.
“Along with standard anti-malware/firewalls, accountants should be using complex 12-character passwords, multi-factor authentication software such as DUO and Okta, or a physical device such as Yubikey, using the cloud for all file storage (no local C-drive data), and installing 3M Privacy Filter screens on displays and laptops,” Right Networks director of firm technology strategy Roman Kepczyk told us. He also suggests disallowing the use of public Wi-Fi (use the mobile hotspot features in a phone instead), disallowing USB thumb drives (use digital portals/secure email instead), and mandating security and phishing training. He also suggests that firms review and update their IT and security policies in areas such as remote work, “bring your own device,” internet access, and other vulnerable areas, and that they buy first- and third-party cyber insurance to reimburse the practice if systems are breached.
Withum’s Bourke is also a proponent of multi-factor authentication: “With the continued migration to the cloud and the use of online applications, implementing a multi-factor authentication tool is not an option! There are so many tools on the market today. I see DUO getting tremendous traction across audit, tax and advisory.”
But Lawton pointed out, “When budgeting for security tools, make sure you also budget for the training needed to use the tools. Too often companies buy expensive, high-end tools but fail to train staff on their usage, so the tools are effectively worthless.”
“Accountants should be using a password manager, like LastPass, a form of multi-factor authentication, and cloud accounting software that is sufficiently secure.” said Cassidy Jakovickas, the CEO and president of MBS Accountancy, a QuickBooks partner.
Added James Slaby, director of cyber protection at security solution vendor Acronis Software, “Enforce strong authentication discipline (two-factor authentication, long passwords, and no password re-use across accounts) to thwart attacks that take advantage of the many huge data breaches in recent years.”
Wolters Kluwer’s Diffin pointed out that tools aren’t a complete solution. “It is paramount to have a written policy in place for firms’ client data security,” he said. “This policy should cover all key IT security aspects. Both digital and physical policies should be reviewed at least annually, and it’s a good idea to perform vulnerability assessments and threat modeling to ensure compliance and safety.”
The need for a plan to recognize threats, and protect yourself and your clients from them, is one area where our respondents agree. Thomson Reuters’ Hackett spelled out one approach: “Essentially there are five steps involved in developing and implementing a written information security plan to safeguard taxpayer data. These are: Perform a risk assessment; design and implement a written information security program; monitor and test this program regularly; provide privacy notices and practices to clients; and evaluate and adjust your program in light of relevant circumstances.”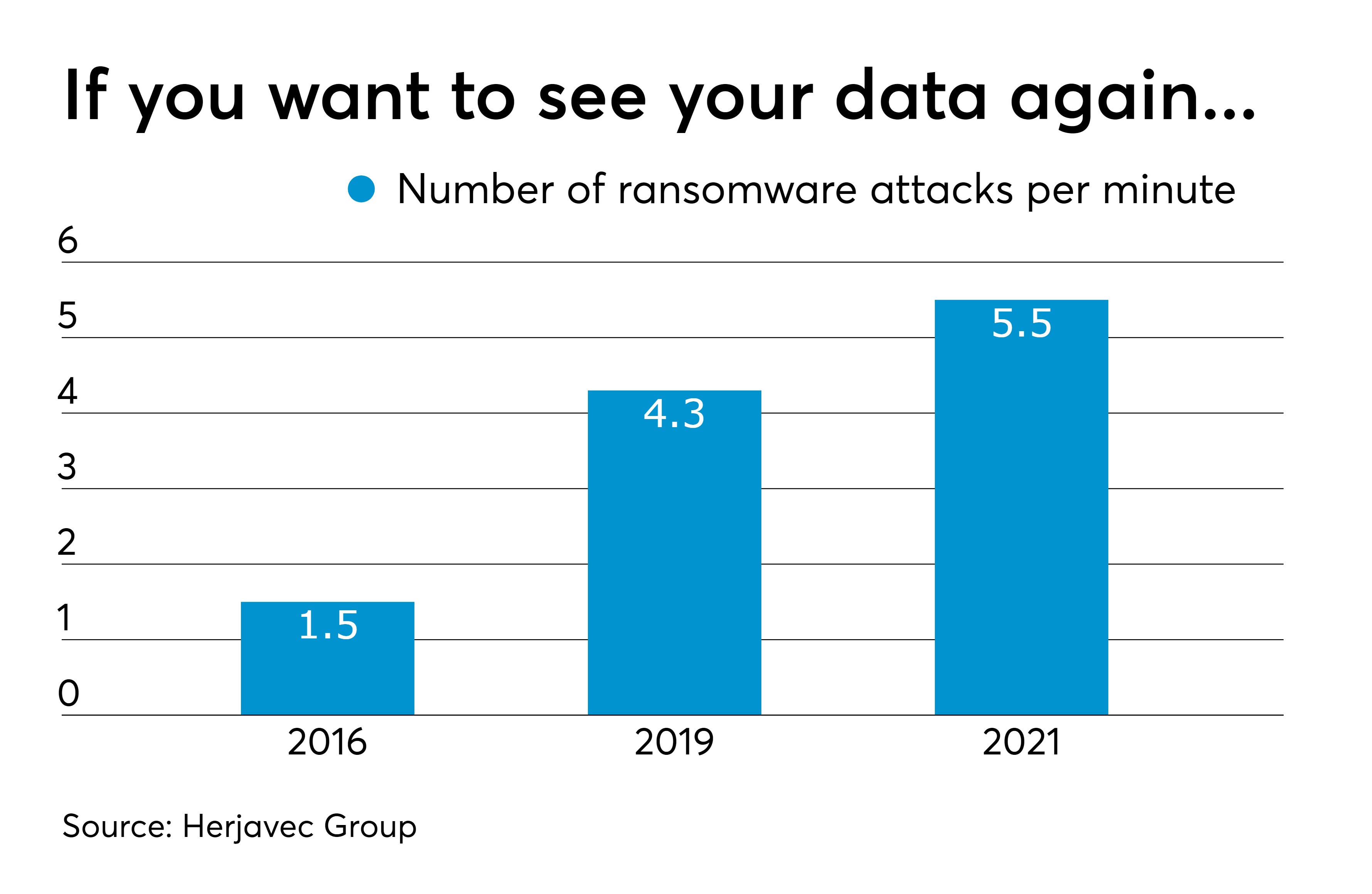 One area of concern is mobile devices. MBS Accountancy’s Jakovickas noted, “It’s increasingly common for companies to allow employees to use their own smartphone or laptop to perform their work duties or access company data. … In these scenarios, however, firms need to remain security-conscious and take steps to protect sensitive data on both company and personal devices.”
One area of concern is mobile devices. MBS Accountancy’s Jakovickas noted, “It’s increasingly common for companies to allow employees to use their own smartphone or laptop to perform their work duties or access company data. … In these scenarios, however, firms need to remain security-conscious and take steps to protect sensitive data on both company and personal devices.”
She continued, “Some general best practices for ensuring employee devices remain reasonably secure include … using a mobile device management software solution to control and erase company data, if necessary, from an employee’s device if it’s lost or stolen, and setting up an employee exit plan that includes items like disabling company emails and removing access to company login credentials.”
You don’t have to go it entirely alone. Many software vendors are well aware of the risks, and build a variety of security features into their software. Acronis’ Slaby pointed out some of the ways that software vendors try and protect customers: “There’s a battery of techniques for this including application vulnerability scanning, secure development practices, application firewalls, and two-factor authentication.”
Oracle NetSuite’s approach is a common one among vendors. “At NetSuite, we employ stringent round-the-clock monitoring tools, policies, and a dedicated security team to help ensure a secure platform for our customers,” Kelly told us. “Having these processes in place allows organizations, regardless of size, to benefit from secure business applications which can otherwise be expensive and onerous to manage in-house”
And Wolters Kluwer’s Diffin detailed some of the measures that his company employs: “Additional security measures are continually being added across the enterprise, including automated functionality that allows employees to quickly and easily report suspicious emails, new features for easy encryption of emails with sensitive information, email banners identifying all external emails, and an Office 365 Data Loss Prevention solution to help prevent sensitive data from leaving the Wolters Kluwer environment.”
When all else fails
Acronis’ Slaby warned, “It’s best to assume that at some point an attack will get through these defenses. Again, this is where behavioral solutions will save your bacon. It’s also wise not to overlook investing in mitigation and recovery, which means formulating plans to respond to a successful attack, ensuring everyone knows who’s in charge and who to call, and then routinely conducting the equivalent of fire drills to test and rehearse your response. All it takes is one unwary employee to invite an attack in, at which point your ability to effectively and quickly recover from the damage will be your best lifeline.”
Finally, keep in mind that cybersecurity is a moving target. Almost all of the vendors and consultants that we spoke with mentioned that as threats evolve, so do the tools, techniques and other ways of dealing with them. Keeping up to date about what your practice and clients face, as well as the means to address them, is not only practical, but in today’s ever-threatening environment, critical.